Table of Links
1.3 Our Work and Contributions and 1.4 Organization
-
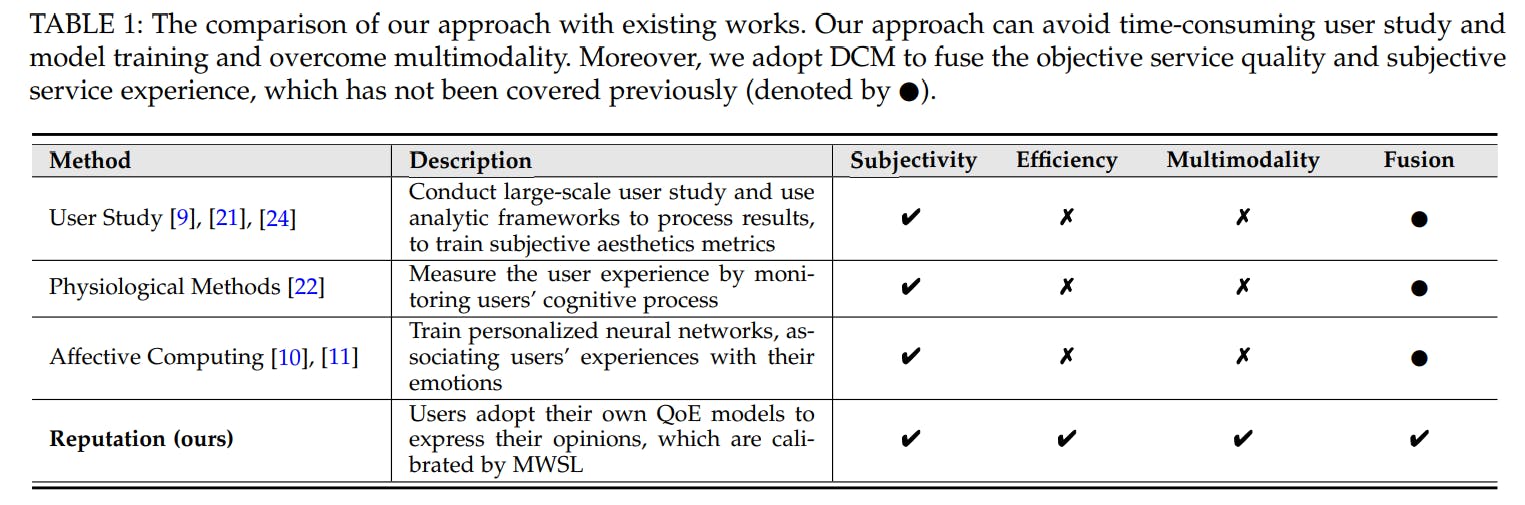
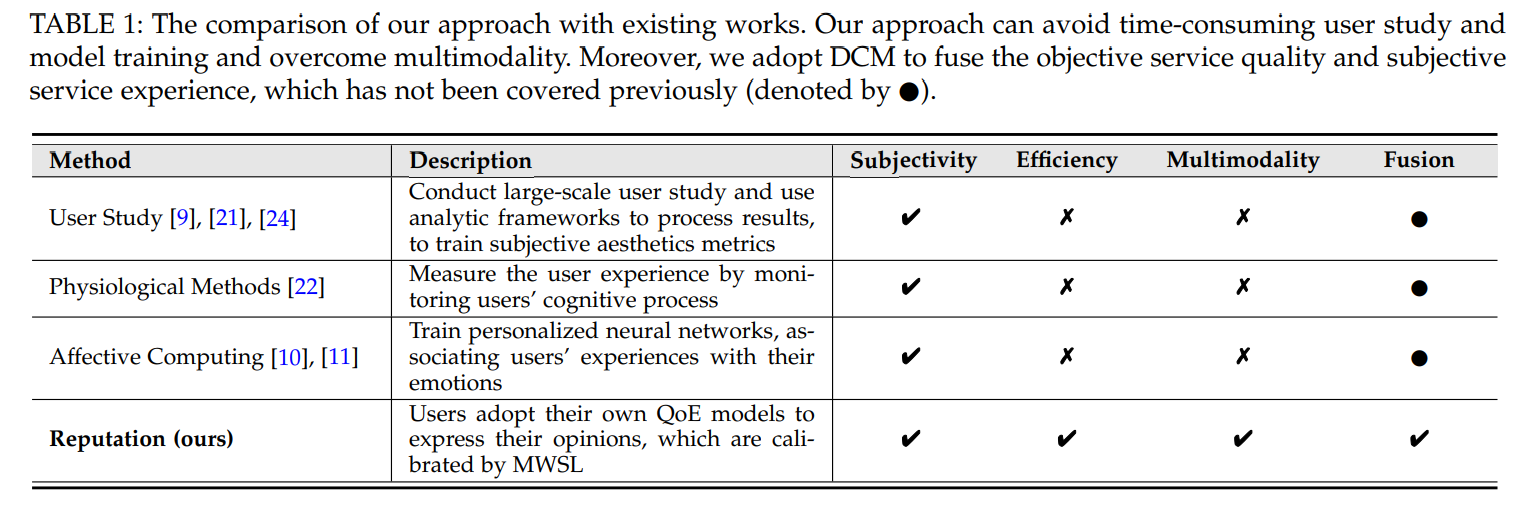
Related Work
-
Prosecutor Design
-
OS2a: Objective Service Assessment for Mobile AIGC
-
OS2A on Prosecutor: Two-Phase Interaction for Mobile AIGC
-
Implementation and Evaluation
7.1 Implementation and Experimental Setup
7.2 Prosecutor Performance Evaluation
3 PRELIMINARIES
In this section, we describe the preliminaries, including the system and threat models of the mobile AIGC and the corresponding design goals of ProSecutor.
3.1 System Model: Mobile AIGC

Given the resource constraints, clients can hardly generate AIGC outputs locally [38]. Instead, with abundant physical resources and professionality to operate AIGC models, the MASPs using mobile-edge servers, can perform AIGC inferences for clients according to the given prompts. Accordingly, they make profits by leasing their computation power to clients. The attackers may launch malicious attacks to compromise security. Without disturbance from attackers, the interaction between clients and MASPs in each round of mobile AIGC service involves three mechanisms, namely MASP selection, payment scheme, and fee-ownership transfer (see Fig. 1-Part B).
3.2 Threat Model
We consider a probabilistic polynomial-time Byzantine adversary [39] in public mobile networks to corrupt MASPs as attackers. Attackers can attempt to destroy ProSecutor system in arbitrary manners. In the following sections, we will discuss eight potential attack strategies and the corresponding defenses of ProSecutor. We then make two assumptions: 1) at most 50% of MASPs can be attackers at any moment, which is the prerequisite for blockchain-empowered security [33], and 2) the attackers are computationally bounded and cannot defeat the modern cryptography algorithms in polynomial time [40]. Note that both the MASPs and clients might be dishonest in pursuing higher profits. For example, since the behaviors of MASPs are hidden from clients, the MASPs may intentionally reduce the resources invested in AIGC inferences after accepting the requests, called the moral hazard effect. Likewise, clients may misbehave by canceling the payment immediately after receiving the AIGC outputs. Last but not least, we consider a practical mobile network where the MASPs and clients are anonymous to each other, without mutual trust [41].
3.3 Design Goals
Given the above system and threat models, we summarize four design goals for ProSecutor to protect mobile AIGC.
• High Adaptability: Before the functional goals, ProSecutor should first fit the mobile AIGC environment, with resource limitations, high workload, and the requirement for processing large AIGC outputs (G1).
• Efficient MASP Selection: The quality and experience of multimodal mobile AIGC services should be measured rationally and efficiently, thereby enabling each client to select the best MASP (G2).
• Optimal Payment Scheme: The clients should produce appropriate payment schemes with MASPs according to the service configurations. Moreover, the moral hazard should not damage the clients’ profits (G3).
• Atomic Fee-ownership Transfer: The execution of the fee-ownership transfers should be atomic, i.e., either the client and MASP receive the output ownership and service fee respectively, or the entire transfer is canceled, without intermediate possibility (G4).
Authors:
(1) Yinqiu Liu, School of Computer Science and Engineering, Nanyang Technological University, Singapore ([email protected]);
(2) Hongyang Du, School of Computer Science and Engineering, Nanyang Technological University, Singapore ([email protected]);
(3) Dusit Niyato, School of Computer Science and Engineering, Nanyang Technological University, Singapore ([email protected]);
(4) Jiawen Kang, School of Automation, Guangdong University of Technology, China ([email protected]);
(5) Zehui Xiong, Pillar of Information Systems Technology and Design, Singapore University of Technology and Design, Singapore ([email protected]);
(6) Abbas Jamalipour, School of Electrical and Information Engineering, University of Sydney, Australia ([email protected]);
(7) Xuemin (Sherman) Shen, Department of Electrical and Computer Engineering, University of Waterloo, Canada ([email protected]).
This paper is