Table of Links
1.3 Our Work and Contributions and 1.4 Organization
-
Related Work
-
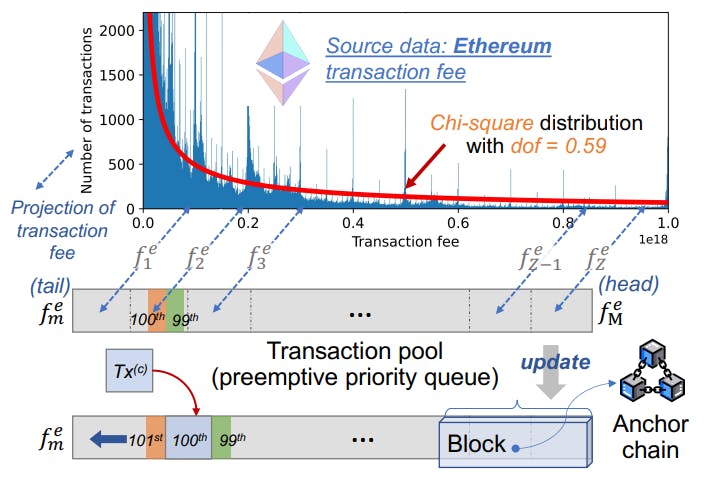
Prosecutor Design
-
OS2a: Objective Service Assessment for Mobile AIGC
-
OS2A on Prosecutor: Two-Phase Interaction for Mobile AIGC
-
Implementation and Evaluation
7.1 Implementation and Experimental Setup
7.2 Prosecutor Performance Evaluation
2.2 Blockchain for Mobile Networks
Two categories of research exist in the field of mobileoriented blockchains. Firstly, as a secure computing platform, blockchain can help mobile networks in various aspects, including key management [25], resource management [26], task offloading [27], mobile crowdsensing [28], and data/resource trading [29]. The general idea is to use blockchains to provide an immutable and traceable ledger and save all the sensitive historical data on-chain, thus defending the malicious tampering [25]. Moreover, blockchain supports Turing-complete smart contracts, which can implement any application logic and are executed automatically when pre-defined conditions are met. Hence, the dependence on mutual trust between mobile devices can be eliminated [30], [31].
Although showing great potential in mobile deployment, traditional blockchains (e.g., Bitcoin and Ethereum) are resource-intensive [30] since every participant performs the consensus mechanism, saves the entire ledger copy, and synchronizes the network-wide messages. Hence, the second research direction is blockchain optimization, making it affordable for resource-constrained mobile devices. For instance, Zaman et al. [32] present a lightweight mobile-oriented consensus mechanism called Proof-of-Sincerity, which reduces the overall consensus costs by encouraging collaboration among devices. Furthermore, Xu et al. [33] jointly consider the computation, storage, and communication resources consumed by blockchain and propose the resource-efficient consensus mechanism, ledger pruning, and fast synchronization, respectively. The emerging sharding technique has also been used in mobile blockchain, alleviating the overhead on each device [34]. These methods aim to refine the architectural design of blockchains, called Layer-1 methods. Accordingly, the optimizations by building additional infrastructures, such as micropayment channels [35], atop blockchains are Layer-2 methods. Finally, assisted by mobile edge computing, the computation-intensive tasks of mobile devices can be offloaded to the edge servers with sufficient physical resources [36], [37].
Insights: Motivated by this, we pay great attention to optimizing the architecture of ProSecutor, making it adapt to the mobile environment when meeting the functional goals. Hence, we propose the reputation roll-up and the duplex transfer channels to improve the efficiency of the two most frequently executed operations in ProSecutor, namely reputation update and fee-ownership transfer.
Authors:
(1) Yinqiu Liu, School of Computer Science and Engineering, Nanyang Technological University, Singapore ([email protected]);
(2) Hongyang Du, School of Computer Science and Engineering, Nanyang Technological University, Singapore ([email protected]);
(3) Dusit Niyato, School of Computer Science and Engineering, Nanyang Technological University, Singapore ([email protected]);
(4) Jiawen Kang, School of Automation, Guangdong University of Technology, China ([email protected]);
(5) Zehui Xiong, Pillar of Information Systems Technology and Design, Singapore University of Technology and Design, Singapore ([email protected]);
(6) Abbas Jamalipour, School of Electrical and Information Engineering, University of Sydney, Australia ([email protected]);
(7) Xuemin (Sherman) Shen, Department of Electrical and Computer Engineering, University of Waterloo, Canada ([email protected]).
This paper is